Started playing around with OpenWRT in a VM on my proxmox instance with the goal of converting that eventually to be my main router. However, before that I wanted to make sure that I both understand how to configure and work with OpenWRT as well as test my potential setup without disrupting production usage in the home 🙂
So, right now the setup looks like below:
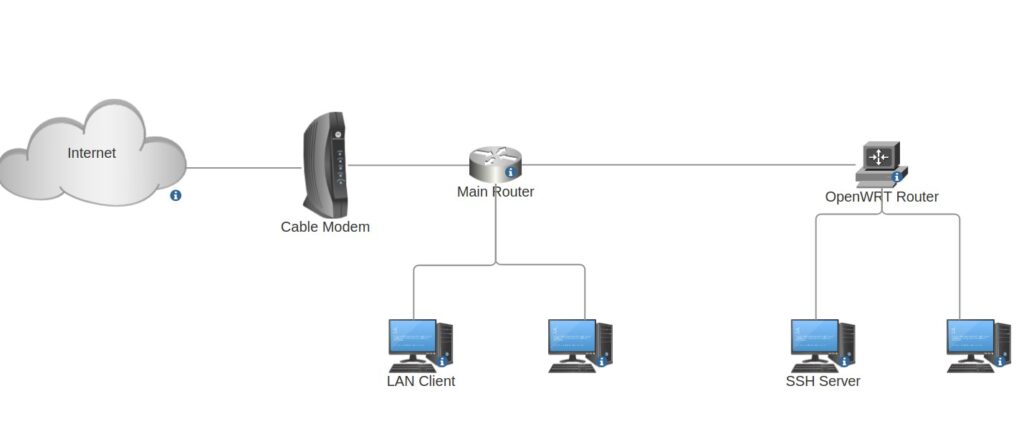
I still have my current router that all my devices are connected to and have OpenWRT running as a VM in my proxmox server. I also have containers mimicking my various servers and services inside the OpenWRT LAN (SSH Server is one example). My first goal in this setup was to see if I can figure out how to allow SSH connections to both the OpenWRT router itself as well as SSH Server inside the OpenWRT LAN from my current LAN (so from LAN Client as an example).
There are plenty of guidance on the Internet on how to setup port forwarding or traffic rule for allowing WAN access to SSH on the router itself. However, none of them address setting up rules that will allow both WAN access to SSH on the router as well as SSH access to servers inside.
Here’s how I managed to do it:
- Create a traffic rule that allows SSH traffic through to LAN from WAN. I was hoping that this would actually enable access to the OpenWRT router’s SSH as well if I used the OpenWRT router’s LAN address. Unfortunately, that did not work. I was able to SSH into SSH Server, but the router itself seemed unreachable both through the WAN and LAN IPs for SSH. This is what this rule looks like:
config rule
option name 'Allow-SSH-From-WAN'
list proto 'tcp'
option src 'wan'
option dest 'lan'
option dest_port '22'
option target 'ACCEPT'- Create an additional port forwarding rule that specifically forwards request to WAN IP, Port 22 to OpenWRT LAN IP, Port 22. The main change from the Internet articles is that this port forwarding rule specifies
src_dipto restrict the rule only to apply to the OpenWRT router’s WAN IP address as destination specified by the source (LAN client). Without this, attempts to access SSH Server will fail as the traffic will be rerouted to the OpenWRT LAN. Here’s what this rule looks like:
config redirect
option dest 'wan'
option target 'DNAT'
option name 'Allow-SSH-To-Router-From-WAN'
list proto 'tcp'
option src 'wan'
option src_dip '192.168.11.168'
option src_dport '22'
option dest_ip '192.168.1.1'
option dest_port '22'Here, 192.168.11.168 is the WAN IP of my OpenWRT router and 192.168.1.1 is the LAN IP of my OpenWRT router. This rule states that traffic for 192.168.11.168:22 should be routed to 192.168.1.1:22 when it comes from the WAN.
With both these rules in place, I am able to connect from LAN Client to both SSH Server and OpenWRT router through SSH. Finally, we can also restrict the source IP address range to be bound to my actual LAN subnet (192.168.11.0/24), so connections are only allowed from the LAN and not from any other network.
One last piece is that because my main router does not allow for configuration of static routes, I need to add a static route on my LAN client – on this Linux machine, I use route add 192.168.1.0/24 via 192.168.11.168 which essentially tells the machine to route all traffic to 192.168.1.0/24 subnet to be sent to 192.168.11.168 instead of routing them to my main router which wouldn’t know how to handle it.